Easy application
security
The world's first security platform built by developers, for developers.
Platforms We Work With:
Launch Bloodhound using our API with any of the industry-leading platforms.
Bloodhound has got your back
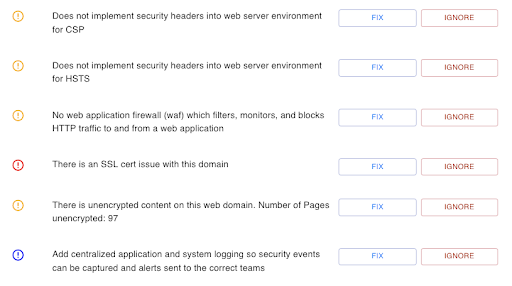
Our platform hunts security gaps in your web applications and offers targeted solutions.
Let Us Revolutionise Your Development Process:
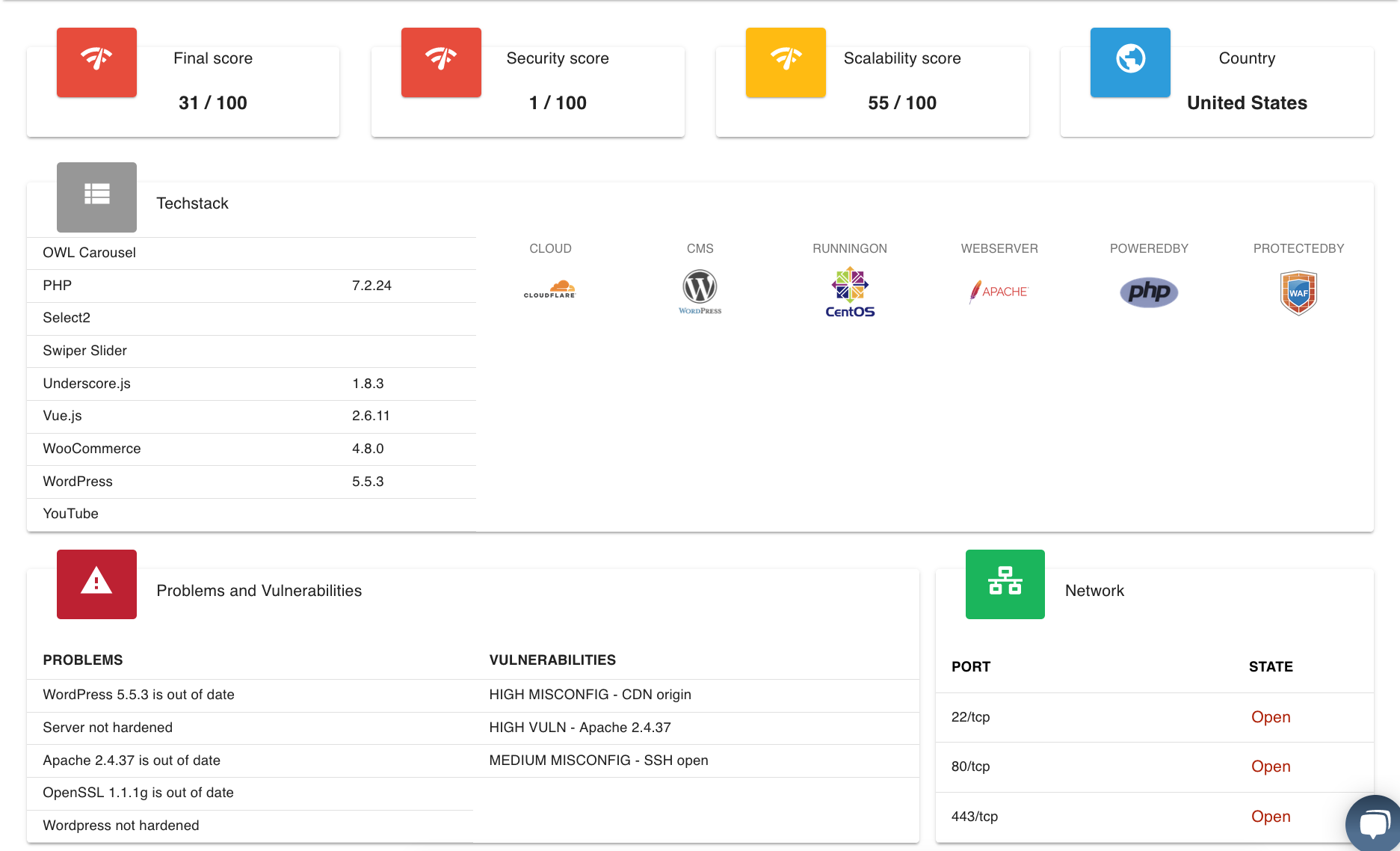
Web Application Analysis
Bloodhound hunts security and availability gaps in your web applications in less than 60 seconds.
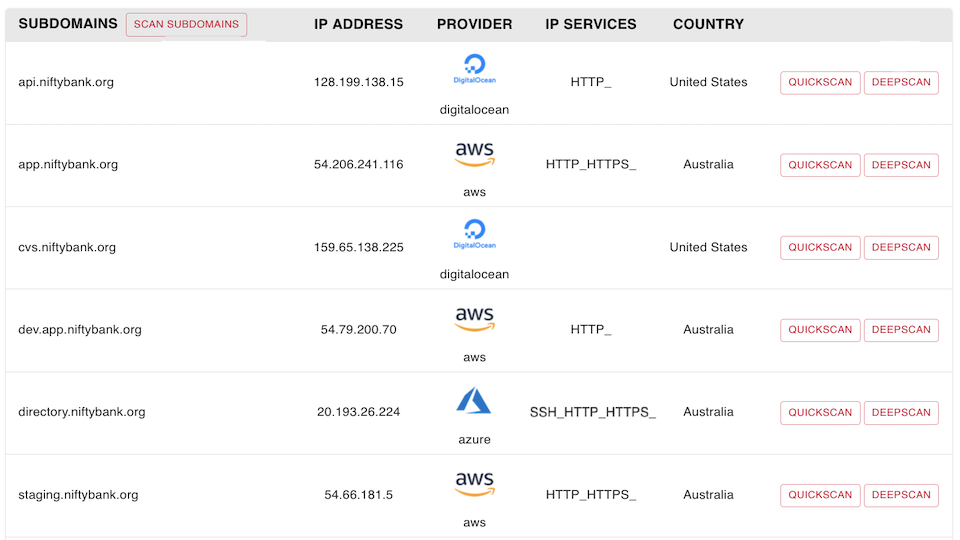
Map the Application Attack Surface & View Your Assets
See what a hacker can see when they view your applications.
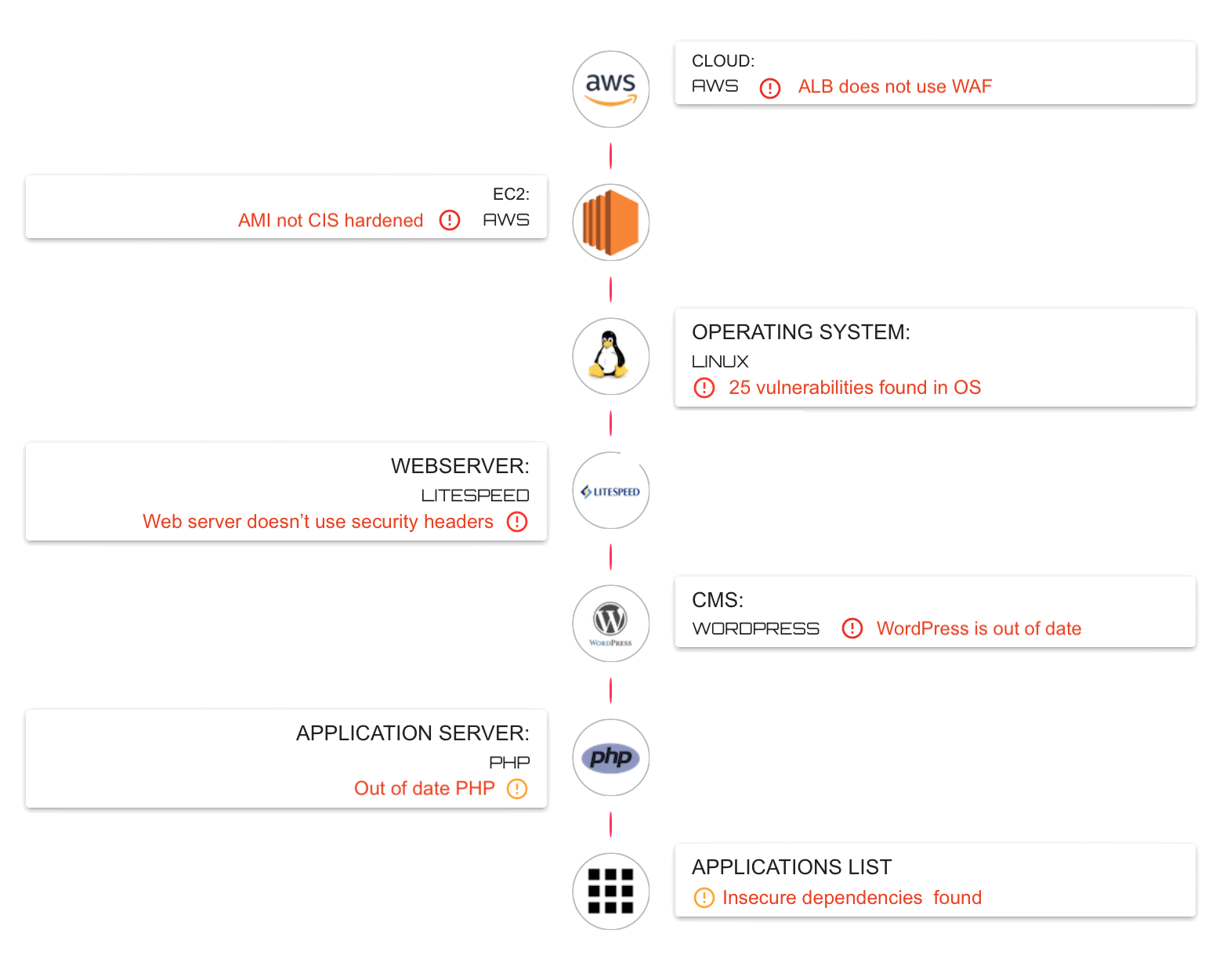
Audit Cloud Dependencies & Resources
Deep dive into the architecture of your web applications.
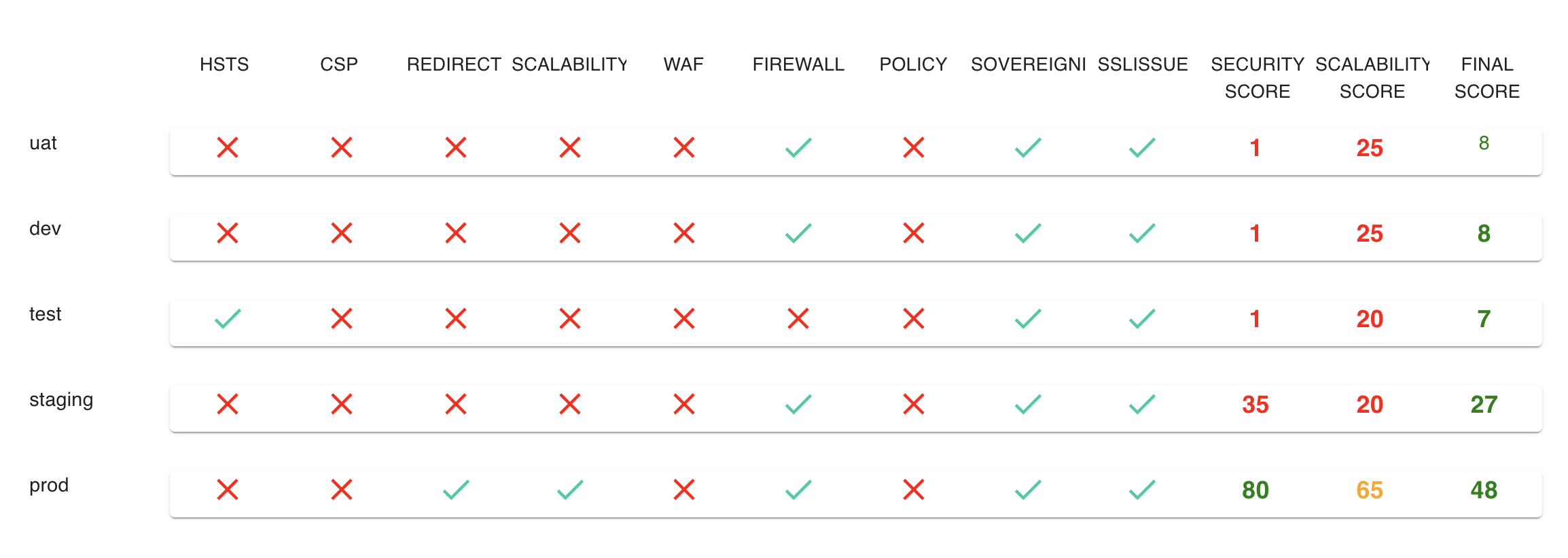
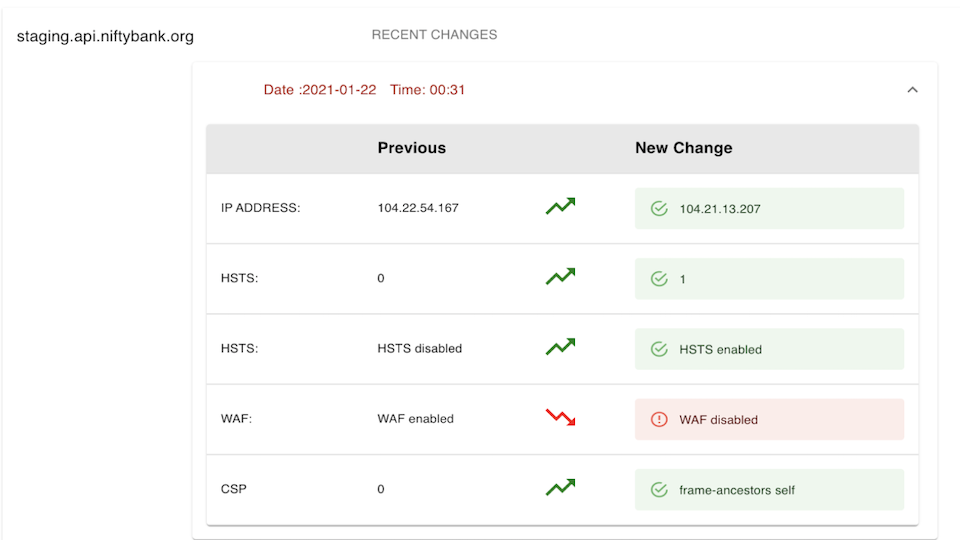
Identify Differences Between Your Environments
Test and compare your development, staging and production environments to quickly find critical differences and understand ways to fix high priority defects.
Monitor Via Your Dashboard
We help you decompose your web application so you are aware of all the resources your app is using behind the scenes.
Embed Fixes Into Your Existing CI/CD Processes
With triggers in the CI/CD pipeline, different environments are constantly being observed and compared.
Access Insights & Solutions
Gain deeper insights around why a specific control is important and how our guardrails will guide you and help your application be more secure.
Track Changes With Every Git Push
Understanding the broad effects and the on-going changes is hard. Bloodhound makes it easy to track with every git push if your application is net-better or net-worse than the previous version.
How is Bloodhound Different?
Made By Developers - For Developers
Bloodhound is the world’s first security platform built by developers, for developers.
Boost your development velocity
Continuous improvement to achieve a faster time to business and shrink your app attack surface by up to 70%.
Easily embed our unique git-centric tools
Into your existing development processes.
Asset discovery and attack surface mapping
Find and fix vulnerabilities, fast and without you needing to become a security expert.
Achieve peace of mind
Provide a sanity check on your deployment.
Test and compare your development, staging and production environments
To quickly find critical differences and understand ways to fix high priority defects.